Due to the WannaCry/WCRY Ransomware attack around 150 counties, we need to notify how our security product to against this attack. The following is the information for protect your origination.

For the Forigatet product:
Update the IPS signature and anti-virus signature
http://blog.fortinet.com/2017/05/12/protecting-your-organization-from-the-wcry-ransomware

For TippingPoint product:
Login to the TMC account https://tmc.tippingpoint.com/TMC/ and download the Ransom_WCRY_i.csw DV toolkit and import to the IPS
The filters in the CSW are designed to detect the propagation of the malware known as WannaCry/WCRY by looking for the malware binary download.

For Sophos UTM:
Active the Advanced Threat Protection in the firewall
https://community.sophos.com/products/unified-threat-management/f/network-protection-firewall-nat-qos-ips/91927/utm-advanced-threat-protection-blocks-kill-switch-url-for-wannacry-also-referenced-as-wcry-wannacrypt-and-wanacrypt0r

For Sophos Intercept X:
https://community.sophos.com/products/intercept/f/information/91942/intercept-x-releasing-any-new-updates-for-wannacry-ransomware/332939

For Lumension:
Apply the latest Windows Patch MS17-010 for all Windows computers by Lumension
https://www.lumension.com/vulnerability-management/patch-management-software.aspx
For Splunk:
Steering Clear of the “WannaCry” or “Wanna Decryptor” Ransomware Attack
https://www.splunk.com/blog/2017/05/13/steering-clear-of-the-wannacry-or-wanna-decryptor-ransomware-attack.html
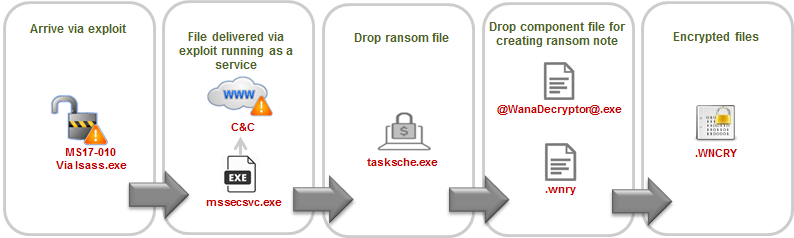
On the 2nd Phase of the Infection Chain, the mssecscr.exe will call back to C&C for the key and OpenDNS will terminate the connection between victim the C&C. This will prevent the exploit of the Wannacry
For questions or technical assistance, please contact Bread Wong or (852) 28510271 (Office).



