
WannaCryptor Ransomware hit over 40 UK hospitals, as well as over 75,000 additional workstations in 99 countries as of today, in what is turning to be the most massive ransomware campaign to date.
The ransomware, also referred to as WannaCry and Wana Decrypt0r, is delivered as a Trojan, which is downloaded when the user mistakenly clicks on a hyperlink delivered in a phishing email, Dropbox link or banner. Once the ransomware payload is executed, it encrypts files on the user’s hard drive, deletes the originals and displays the following message, requesting the user to pay a ransom in order to decrypt and recover the files.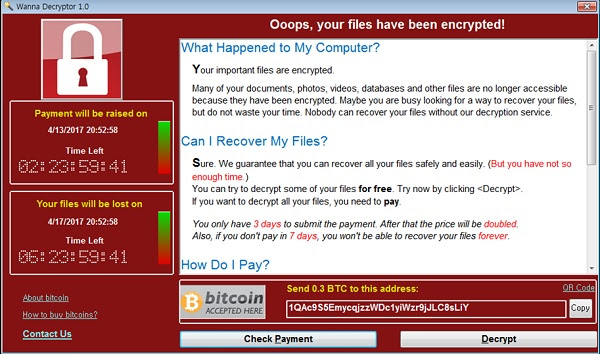
Why is WannaCryptor ransomware spreading so quickly?
As initially reported by the Spanish CERT, and confirmed by Cyberbit researchers, the attack utilizes a Windows XP vulnerability: EternalBlue/MS17-010/SMB to spread laterally. This means that after attacking one computer in the organization, the ransomware can spread independently within the network and attack additional workstations. An interesting fact is that this exploit was developed by the NSA and leaked by Shadow Brokers hacker group. Although these vulnerabilities were patched by Microsoft in March, large corporates, particularly hospitals, often lag behind in patching and therefore many of the workstations were left vulnerable, allowing the attack to spread.
What should your organization do now?
1. Patch Windows XP machines immediately – while this will not prevent the initial infection it will prevent the ransomware from spreading laterally and substantially slow it down
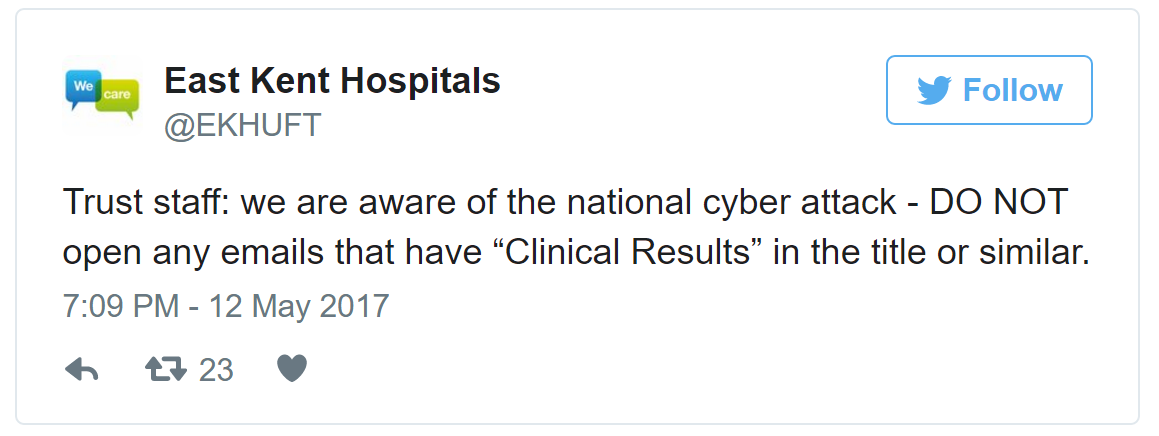
2. Re-enforce security awareness best practices – East Kent Hospitals Tweeted all staff and warned them from opening the phishing email labeled ‘Clinical results’. Update your employees on best practices and warn them about the risk of opening unexpected emails from untrusted or sources
Wannacryptor Ransomware
3. Deploy an Endpoint Detection and Response Product with anti-ransomware – only 30% of antivirus software can identify and block WannaCryptor ransomware, as reported by the Mirror. It is essential to complement antivirus with an endpoint detection and response product that protects against advanced malware that bypasses traditional AV. This solution should include inherent anti-ransomware capabilities to block.
Cyberbit EDR anti-ransomware
Cyberbit’s Endpoint Detection and Response (EDR) provides ransomware detection and prevention that helps organizations detect and block ransomware attacks like WannaCryptor in real-time before critical files were encrypted. Cyberbit EDR identifies behavioral characteristics that indicate an attack, and as a result it detects threats that often bypass antivirus solutions.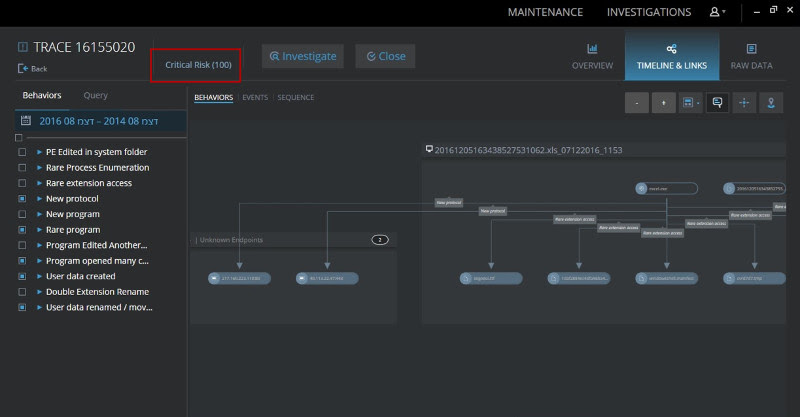
Cyberbit EDR graph view – identifying ransomware infection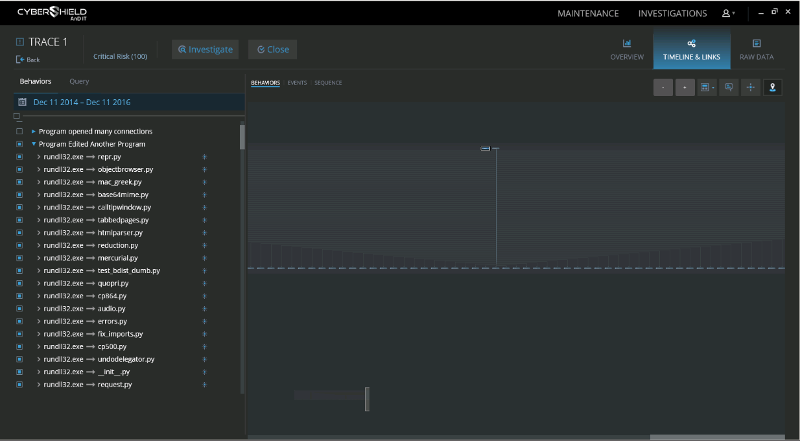
Cyberbit EDR – Identifying ransomware encryption behavior
Read the Cyberbit blog for recent ransomware detection success story in a large enterprise and visit the Cyberbit website for more info and a demo
Tal Morgenstern is Head of R&D, Endpoint Detection and Response Team at Cyberbit.
Please feel free to contact us for more information.



