-
Authentication (5)
We provide strong multi factor authentication (such as contactless smartcard, contact smartcard, fingerprint, PIN, PKI) solution for remote access (i.e VPN, Outlook Web Access, Citrix, IIS), windows logon and physical door access. -
Data Encryption (7)
Data contains company's critical business information should be safeguarded from unauthorized access. We provide multiple different encryption solution (such as file encryption, folder encryption, disk encryption, database encryption, transaction encryption) to help you to safeguard such data no matter the data is in rest or exchanged. -
Desktop / Endpoint Management (10)
Our enterprise grade desktop management solution provide an easy and efficient way to manage the various desktop issues (such as patch management, software and hardware inventory, desktop security policy, remote access) from a centralize perspective. -
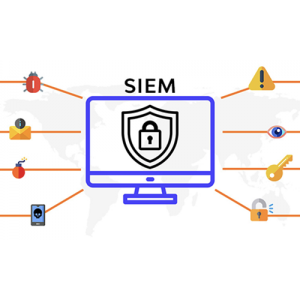
Email Security (8)
Email is one the most important business application today. We provide email security solution which can protect the confidentiality of your email communication, prevent virus attack, filter spam mail, as well as help you to comply the related security compliance requirements. -
Network Security (8)
Network security is a key to protect company IT infrastructure. It is the fundamental measure to ensure a secure environment for company business operation. We provide cost effective network security solutions to help company to protect their IT asset from malware, virus, and other network attacks and the same time our network security product can also enable company to maximum the performance and investment return on the… -
Security Audit and Assessment (7)
A Security Audit is an extensive and formal overview of an organization’s security systems and processes. The audit is an all-encompassing, in-depth, review of not only physical attributes (networks, firewalls, hardware, etc.) but other areas including policy and standard operating procedures. Security Assessment is generally referring to a Vulnerability Assessment which scans an organization’s infrastructure and identifies vulnerabilities (faulty firewall, lack of system updates, malware, etc.). With… -
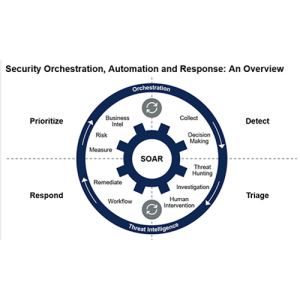
Security Orchestration, Automation and Response (2)
SOAR (Security Orchestration, Automation and Response) is a solution stack of compatible software programs that allow an organization to collect data about security threats from multiple sources and respond to low-level security events without human assistance. -
Wi-Fi Solution (4)
Our Wifi solution helps simplify networking by reducing the cost and complexity of distributed enterprise deployments with cloud-enabled networking solutions. These solutions, based on our unique distributed intelligence architecture, include enterprise-class Wi-Fi access points and revolutionary, easy-to-deploy routers.
-
Authentication (5)
We provide strong multi factor authentication (such as contactless smartcard, contact smartcard, fingerprint, PIN, PKI) solution for remote access (i.e VPN, Outlook Web Access, Citrix, IIS), windows logon and physical door access. -
Data Encryption (7)
Data contains company's critical business information should be safeguarded from unauthorized access. We provide multiple different encryption solution (such as file encryption, folder encryption, disk encryption, database encryption, transaction encryption) to help you to safeguard such data no matter the data is in rest or exchanged. -
Desktop / Endpoint Management (10)
Our enterprise grade desktop management solution provide an easy and efficient way to manage the various desktop issues (such as patch management, software and hardware inventory, desktop security policy, remote access) from a centralize perspective. -
Email Security (8)
Email is one the most important business application today. We provide email security solution which can protect the confidentiality of your email communication, prevent virus attack, filter spam mail, as well as help you to comply the related security compliance requirements. -
Network Security (8)
Network security is a key to protect company IT infrastructure. It is the fundamental measure to ensure a secure environment for company business operation. We provide cost effective network security solutions to help company to protect their IT asset from malware, virus, and other network attacks and the same time our network security product can also enable company to maximum the performance and investment return on the… -
Security Audit and Assessment (7)
A Security Audit is an extensive and formal overview of an organization’s security systems and processes. The audit is an all-encompassing, in-depth, review of not only physical attributes (networks, firewalls, hardware, etc.) but other areas including policy and standard operating procedures. Security Assessment is generally referring to a Vulnerability Assessment which scans an organization’s infrastructure and identifies vulnerabilities (faulty firewall, lack of system updates, malware, etc.). With… -
Security Orchestration, Automation and Response (2)
SOAR (Security Orchestration, Automation and Response) is a solution stack of compatible software programs that allow an organization to collect data about security threats from multiple sources and respond to low-level security events without human assistance. -
Wi-Fi Solution (4)
Our Wifi solution helps simplify networking by reducing the cost and complexity of distributed enterprise deployments with cloud-enabled networking solutions. These solutions, based on our unique distributed intelligence architecture, include enterprise-class Wi-Fi access points and revolutionary, easy-to-deploy routers.
-
Authentication (5)
We provide strong multi factor authentication (such as contactless smartcard, contact smartcard, fingerprint, PIN, PKI) solution for remote access (i.e VPN, Outlook Web Access, Citrix, IIS), windows logon and physical door access. -
Data Encryption (7)
Data contains company's critical business information should be safeguarded from unauthorized access. We provide multiple different encryption solution (such as file encryption, folder encryption, disk encryption, database encryption, transaction encryption) to help you to safeguard such data no matter the data is in rest or exchanged. -
Desktop / Endpoint Management (10)
Our enterprise grade desktop management solution provide an easy and efficient way to manage the various desktop issues (such as patch management, software and hardware inventory, desktop security policy, remote access) from a centralize perspective. -
Email Security (8)
Email is one the most important business application today. We provide email security solution which can protect the confidentiality of your email communication, prevent virus attack, filter spam mail, as well as help you to comply the related security compliance requirements. -
Network Security (8)
Network security is a key to protect company IT infrastructure. It is the fundamental measure to ensure a secure environment for company business operation. We provide cost effective network security solutions to help company to protect their IT asset from malware, virus, and other network attacks and the same time our network security product can also enable company to maximum the performance and investment return on the… -
Security Audit and Assessment (7)
A Security Audit is an extensive and formal overview of an organization’s security systems and processes. The audit is an all-encompassing, in-depth, review of not only physical attributes (networks, firewalls, hardware, etc.) but other areas including policy and standard operating procedures. Security Assessment is generally referring to a Vulnerability Assessment which scans an organization’s infrastructure and identifies vulnerabilities (faulty firewall, lack of system updates, malware, etc.). With… -
Security Orchestration, Automation and Response (2)
SOAR (Security Orchestration, Automation and Response) is a solution stack of compatible software programs that allow an organization to collect data about security threats from multiple sources and respond to low-level security events without human assistance. -
Wi-Fi Solution (4)
Our Wifi solution helps simplify networking by reducing the cost and complexity of distributed enterprise deployments with cloud-enabled networking solutions. These solutions, based on our unique distributed intelligence architecture, include enterprise-class Wi-Fi access points and revolutionary, easy-to-deploy routers.